Rapidshare Hack
There are two hacks to beat Rapidshare download limits and waiting time.
1) Rapidshare Hack (For Firefox Users) :-
The hot new Firefox plug-in takes browser customization to a whole new level by letting users filter site content or change page behaviors.
The glory of open-source software is that it allows anyone with the inclination and the scripting knowledge to get under the hood and hot-rod their computing environment.
But most of the time, that advantage is available only to people with the programming skills to make the changes they want.
That's where Greasemonkey, a free plug-in for Firefox, comes in -- it simplifies hacking the browser.
Released at the end 2004, Greasemonkey is the latest in a growing arsenal of Firefox customization tools.
It changes how Web pages look and act by altering the rendering process.
http://greasemonkey.mozdev.org/
1) Install the Greasemonkey extension>>
http://downloads.mozdev.org/greasemonkey/greasemonkey_0.2.6.xpi
2) Restart Firefox
3) Go to http://rapidshare.de/files/1034529/rapidshare.user.js.html
4) Right click on rapidshare.user.js and choose "Install User Script".
5) Run FireFox.
6) From 'File' Menu click on Open File then browse to whereever you saved the 'greasemonkey.xpi' plug-in.
Open it, wait a couple seconds for the install button becomes active.
7) Click on it to install this plug-in then CLOSE FIREFOX.
8) Run FireFox again.
From the File Menu click on Open File then browse to whereever you saved the 'rapidshare.user.js'.
9) Open it.
10) Click the Tools Menu then click on Install User Script then click OK.
11) Close FireFox.
The script will let you enjoy "no wait" and multiple file downloads......!
2) Rapidshare Hack (NIC Tricks and MAC Cloning) :-
Rapidshare traces the users IP address to limit each user to a certain amount of downloading per day.
To get around this, you need to show the rapidshare server a different IP address.
Here are some methods for doing this-
A] Short-Out the JavaScript:
1) Goto the page you want to download
2) Select FREE button
3) In the address bar put this- javascript:alert(c=0)
4) Click OK
5) Click OK to the pop-up box
6) Enter the captcha
7) Download Your File
B] Request a new IP address from your ISP server:
Here’s how to do it in windows:
1) Click Start
2) Click run
3) In the run box type cmd.exe and click OK
4) When the command prompt opens type the following. ENTER after each new line.
ipconfig /flushdns
ipconfig /release
ipconfig /renew
exit
5) Erase your cookies in whatever browser you are using.
6) Try the rapidshare download again.
Frequently you will be assigned a new IP address when this happens.
Sometime you will, sometimes you will not. If you are on a fixed IP address, this method will not work.
If this works for you, you may want to save the above commands into a batch file, and just run it when you need it.
C] Use a proxy with SwitchProxy and Firefox:
1) Download and install Firefox
2) Download and install SwitchProxy
3) Google for free proxies
4) When you hit your download limit, clean your cookies and change your proxy
D] You can use a bookmarklet to stop your wait times:
1) Open IE
2) Right Click On This Link
3) Select Add to Favorites
4) Select Yes to the warning that the bookmark may be unsafe.
5) Name it “RapidShare No Wait”
6) Click on the Links folder (if you want to display it in your IE toolbar)
7) Click OK
8) You may need to close and reopen IE to see it
9) Goto rapidshare and click the bookmarklet when you are forced to wait
Saturday, December 26, 2009
Access Free Airtel GPRS Using TeaShark Browser
Access Free Airtel GPRS Using TeaShark Browser
TeaShark, a mobile browser like Opera Mini, allow you to access Airtel GPRS for FREE.
Shockingly it has nothing to do with modifying any Airtel settings or any kind of hack.
Here is how I used this…
* Download TeaShark v. 312. Its free and being JAR file it can be installed on most handsets.
* Open it from your mobile and select AirTel Live as access point.
* That’s it! Open any site from TeaShark and you won’t be charged anything.
Note for the first time, when TeaShark starts, it may take more than one minute to initialize. Also this one time initialization may fail many times. But don’t loose your heart!
As of now, this trick is limited to handsets only.
Note:“Subscribe to Packet Data First”
This means you need to activate AirTel Live service which is free.
Contact customer care to get it activated.
Also select only AirTel Live as access point when prompted by TeaShark.
Download TeaShark: http://teashark.com/download.html
TeaShark, a mobile browser like Opera Mini, allow you to access Airtel GPRS for FREE.
Shockingly it has nothing to do with modifying any Airtel settings or any kind of hack.
Here is how I used this…
* Download TeaShark v. 312. Its free and being JAR file it can be installed on most handsets.
* Open it from your mobile and select AirTel Live as access point.
* That’s it! Open any site from TeaShark and you won’t be charged anything.
Note for the first time, when TeaShark starts, it may take more than one minute to initialize. Also this one time initialization may fail many times. But don’t loose your heart!
As of now, this trick is limited to handsets only.
Note:“Subscribe to Packet Data First”
This means you need to activate AirTel Live service which is free.
Contact customer care to get it activated.
Also select only AirTel Live as access point when prompted by TeaShark.
Download TeaShark: http://teashark.com/download.html
Hacking AOL,Yahoo
We get numerous calls from people who want to recover AOL®, Yahoo® or Hotmail® or other online and email passwords. We do not do this type of work. Many of these people claim that they have lost their passwords because they have been hacked and now need to get their password back. As we have reviewed information on the web, we found very little real information about the actual techniques that could be used to hack these services. So we decided to pull together a detailed explanation.
What follows is a detailed explanation of the methodologies involved. We do not condone any illegal activity and we clearly mention in this article techniques that are illegal. Sometimes these methods are known as “Phishing.”
THE HOAX
Let’s dispose of one technique that is absolutely a hoax (meaning a fraud: something intended to deceive; deliberate trickery intended to gain an advantage.) If you see a newsgroup post or web page with something like the following, it is a hoax and will not work.
: : : (([[THIS REALLY WORKS ]])) : : :
(1) send an E-mail to passwordrecovery@yourdomainhere.com
(2) In the subject box type the screenname of the person whose password you wish to steal
(3) In the message box type the following: /cgi-bin/start?v703&login.USER=passmachine&class=supervisor&f={your aol password}&f=27586&javascript=ACTIVE&rsa
(4) Send the e-mail with priority set to “high” (red ! in some mailprograms)
(5) wait 2-3 minutes and check your mail
(6) Read the message.-Where YOUR password was typed before, NOW, the password of the screenname in the code string is there!!!
Why does this work? It´s a special decryption-server that AOL-employees can use to decrypt passwords.The aolbackdoor account is a bot that reads your authentification from the message body and identifiying you as a valid AOL Staff-member, you will get the password mailed back to you. The trick is that this Bot´s script seems to be a little bit buggy and it automatically recogises you as an supervisor (AOL-Staff member), even if you use a normal AOL account. This means, that EVERYONE having a valid AOL account can hack as many other accounts as he wants.
This is just a scam to steal your password and may explain some of the calls we get from people saying they were hacked. Never give your password to anyone. No legitimate web service or customer service representative will ask for it or need it. There is no magic email address or series of commands that will reveal the passwords of users.
LOCALLY STORED PASSWORDS
Most browsers, including Internet Explorer® and Netscape®, the AOL® client, and Windows® Dial-Up Connections allow you the option to store passwords. These passwords are stored on the local machine and (depending upon where and how it is stored) there is usually a method of recovering these passwords. Storing any password locally is insecure and may allow the password to be recovered by anyone who has access to the local machine. While we are not currently aware of any program to recover locally stored AOL® passwords, we do not recommend that these are secure. Software does exist that can recover most of the other types of locally stored passwords.
TROJAN
A Trojan is a program that is sent to a user that allows an attacker to control functions of the target computer, recover information from the target or to delete or damage files on the target. The name Trojan is given because the program will usually come attached to some other program or file that entices you to run it. There are a wide variety of Trojans any number of which can be programmed to capture passwords as they are typed and to email or transmit them to a third party. To protect yourself against Trojans, you should never execute or download software or files that are not from a trusted source. It is critical that anyone working on internet use a virus protection program (which should catch most Trojans.) Note that since a Trojan requires the password to be typed or stored in order to be recovered, this is not an effective way to recover your own password. It could explain, however, how someone could lose their password to a hacker. Sending someone a Trojan program is certainly illegal and we do not recommend or condone this activity. A Trojan is unlikely to be effective in recovering a particular account password since it requires the target to install it. However, hackers will often bulk mail Trojans to thousands of people in the hope that a small percentage will get caught. Legitimate account holders who may have been caught by a Trojan and can authenticate themselves should contact their service provider to have their account passwords reset.
KEYLOGGER
A keylogger is a program or piece of hardware that records all keyboard keystrokes to an encrypted file which can then be read later. Based on the order of the keystrokes, it is usually easy to identify the password(s) from the file later. Like the Trojan, this also requires that someone actually type the password. Keyloggers come in two types: hardware and software. A hardware keylogger can be fitted between the keyboard cable and the computer and can be activated with a few keystrokes. It is then left in place until after the password that you are looking to recover is typed. Later it is removed and the file of keystrokes is examined for the password. A hardware keylogger is undectable by anti-virus software. A software keylogger is installed on a system and effectively has the same function, however, it is a little bit more complex to use since it must be installed to run stealthily to be effective. A keylogger could be used to steal a password from someone who is using an office computer or sharing a computer. It is possible that installing and using such a device or piece of software could be illegal depending upon whether the target has a presumption of privacy when using the computer on which the keylogger is installed.
IMPERSONATION
It is possible to impersonate a program on a computer by launching windows that look like something else. For instance, let’s say you login to the MSN® service and visit a website (in this case a hostile website.) It would be possible for this website to pop-up some windows that look like something else. They could look almost identical to windows that an inexperienced user might expect from his local computer. The user could be fooled into submitting information to the hostile website. For instance, consider the effect of seeing the following series of windows:
If these could trick you into entering your password, then you could end-up sending your password to the attacker. Windows such as these could be created to mirror virtually any program or series of actions. Your browser will likely identify your operating system and your IP address might identify your ISP. Therefore, a hostile website could target you with a series of screen shots that look exactly as they should on your system. The key is that the screen shots are not coming from your system, but are coming from the hostile website. First, creating such a hostile website is probably fraudulent and illegal. We do not recommend or condone this activity. To protect yourself against this type of attack, make sure to configure your browser for high security and enable warnings for any code that is executed on your system.
SNIFFING
If two people do not share the same computer, but do share the same network, it may be possible for one to sniff the others’ packets as they sign-on. The traffic between your computer and the internet site you are accessing may be able to be recorded and decrypted or “played-back.” This is not a simple attack to execute, but is possible if two people are close to one another and share a hub. Again, this is likely to be illegal and we do not condone this activity.
BRUTE-FORCE ATTACK
Many people want to find software to perform a brute-force attack. This is really impractical. It would take hundreds of thousands of years to attempt any kind of reasonable brute-force attack on AOL®, Yahoo® or Hotmail® and this would expand exponentially if the password is longer than the minimum length. Using multiple computers or multiple sessions could reduce this to merely thousands of years. This is highly illegal since these services own the servers on which an account is hosted. Even if you are hacking your own account, you don’t own the servers and the service is going to monitor and log this activity. It is extremely unlikely that you could recover a password in this way, but it is extremely likely that you’d be arrested and prosecuted for doing this.
SOCIAL ENGINEERING
Social engineering is the name given to the art of attacking the person, rather than the computer or system. The basic principle is that many people can be talked into giving someone else their id and password if they think it is someone that they can trust. For instance, I might call someone and say I was from AOL and that I was finally getting around to responding to their technical support question. I would then ask you to describe the problem that you are having and tell you that we have a solution. However, I just need to verify the account. Can you give me the username and password again? A surprising number of people would fall for this obvious scam. There is no limit as to how elaborate this can be. The more information that is given by the caller, the more realistic or believable the call is. Again, never give your password to anyone. No legitimate customer service representative will ask for this information.
These are the basic methods that we are aware of for hacking an AOL®, Yahoo®, Hotmail® or any other dial-up or on-line password. Hopefully this will answer some questions and help you protect yourself against these attacks
What follows is a detailed explanation of the methodologies involved. We do not condone any illegal activity and we clearly mention in this article techniques that are illegal. Sometimes these methods are known as “Phishing.”
THE HOAX
Let’s dispose of one technique that is absolutely a hoax (meaning a fraud: something intended to deceive; deliberate trickery intended to gain an advantage.) If you see a newsgroup post or web page with something like the following, it is a hoax and will not work.
: : : (([[THIS REALLY WORKS ]])) : : :
(1) send an E-mail to passwordrecovery@yourdomainhere.com
(2) In the subject box type the screenname of the person whose password you wish to steal
(3) In the message box type the following: /cgi-bin/start?v703&login.USER=passmachine&class=supervisor&f={your aol password}&f=27586&javascript=ACTIVE&rsa
(4) Send the e-mail with priority set to “high” (red ! in some mailprograms)
(5) wait 2-3 minutes and check your mail
(6) Read the message.-Where YOUR password was typed before, NOW, the password of the screenname in the code string is there!!!
Why does this work? It´s a special decryption-server that AOL-employees can use to decrypt passwords.The aolbackdoor account is a bot that reads your authentification from the message body and identifiying you as a valid AOL Staff-member, you will get the password mailed back to you. The trick is that this Bot´s script seems to be a little bit buggy and it automatically recogises you as an supervisor (AOL-Staff member), even if you use a normal AOL account. This means, that EVERYONE having a valid AOL account can hack as many other accounts as he wants.
This is just a scam to steal your password and may explain some of the calls we get from people saying they were hacked. Never give your password to anyone. No legitimate web service or customer service representative will ask for it or need it. There is no magic email address or series of commands that will reveal the passwords of users.
LOCALLY STORED PASSWORDS
Most browsers, including Internet Explorer® and Netscape®, the AOL® client, and Windows® Dial-Up Connections allow you the option to store passwords. These passwords are stored on the local machine and (depending upon where and how it is stored) there is usually a method of recovering these passwords. Storing any password locally is insecure and may allow the password to be recovered by anyone who has access to the local machine. While we are not currently aware of any program to recover locally stored AOL® passwords, we do not recommend that these are secure. Software does exist that can recover most of the other types of locally stored passwords.
TROJAN
A Trojan is a program that is sent to a user that allows an attacker to control functions of the target computer, recover information from the target or to delete or damage files on the target. The name Trojan is given because the program will usually come attached to some other program or file that entices you to run it. There are a wide variety of Trojans any number of which can be programmed to capture passwords as they are typed and to email or transmit them to a third party. To protect yourself against Trojans, you should never execute or download software or files that are not from a trusted source. It is critical that anyone working on internet use a virus protection program (which should catch most Trojans.) Note that since a Trojan requires the password to be typed or stored in order to be recovered, this is not an effective way to recover your own password. It could explain, however, how someone could lose their password to a hacker. Sending someone a Trojan program is certainly illegal and we do not recommend or condone this activity. A Trojan is unlikely to be effective in recovering a particular account password since it requires the target to install it. However, hackers will often bulk mail Trojans to thousands of people in the hope that a small percentage will get caught. Legitimate account holders who may have been caught by a Trojan and can authenticate themselves should contact their service provider to have their account passwords reset.
KEYLOGGER
A keylogger is a program or piece of hardware that records all keyboard keystrokes to an encrypted file which can then be read later. Based on the order of the keystrokes, it is usually easy to identify the password(s) from the file later. Like the Trojan, this also requires that someone actually type the password. Keyloggers come in two types: hardware and software. A hardware keylogger can be fitted between the keyboard cable and the computer and can be activated with a few keystrokes. It is then left in place until after the password that you are looking to recover is typed. Later it is removed and the file of keystrokes is examined for the password. A hardware keylogger is undectable by anti-virus software. A software keylogger is installed on a system and effectively has the same function, however, it is a little bit more complex to use since it must be installed to run stealthily to be effective. A keylogger could be used to steal a password from someone who is using an office computer or sharing a computer. It is possible that installing and using such a device or piece of software could be illegal depending upon whether the target has a presumption of privacy when using the computer on which the keylogger is installed.
IMPERSONATION
It is possible to impersonate a program on a computer by launching windows that look like something else. For instance, let’s say you login to the MSN® service and visit a website (in this case a hostile website.) It would be possible for this website to pop-up some windows that look like something else. They could look almost identical to windows that an inexperienced user might expect from his local computer. The user could be fooled into submitting information to the hostile website. For instance, consider the effect of seeing the following series of windows:
If these could trick you into entering your password, then you could end-up sending your password to the attacker. Windows such as these could be created to mirror virtually any program or series of actions. Your browser will likely identify your operating system and your IP address might identify your ISP. Therefore, a hostile website could target you with a series of screen shots that look exactly as they should on your system. The key is that the screen shots are not coming from your system, but are coming from the hostile website. First, creating such a hostile website is probably fraudulent and illegal. We do not recommend or condone this activity. To protect yourself against this type of attack, make sure to configure your browser for high security and enable warnings for any code that is executed on your system.
SNIFFING
If two people do not share the same computer, but do share the same network, it may be possible for one to sniff the others’ packets as they sign-on. The traffic between your computer and the internet site you are accessing may be able to be recorded and decrypted or “played-back.” This is not a simple attack to execute, but is possible if two people are close to one another and share a hub. Again, this is likely to be illegal and we do not condone this activity.
BRUTE-FORCE ATTACK
Many people want to find software to perform a brute-force attack. This is really impractical. It would take hundreds of thousands of years to attempt any kind of reasonable brute-force attack on AOL®, Yahoo® or Hotmail® and this would expand exponentially if the password is longer than the minimum length. Using multiple computers or multiple sessions could reduce this to merely thousands of years. This is highly illegal since these services own the servers on which an account is hosted. Even if you are hacking your own account, you don’t own the servers and the service is going to monitor and log this activity. It is extremely unlikely that you could recover a password in this way, but it is extremely likely that you’d be arrested and prosecuted for doing this.
SOCIAL ENGINEERING
Social engineering is the name given to the art of attacking the person, rather than the computer or system. The basic principle is that many people can be talked into giving someone else their id and password if they think it is someone that they can trust. For instance, I might call someone and say I was from AOL and that I was finally getting around to responding to their technical support question. I would then ask you to describe the problem that you are having and tell you that we have a solution. However, I just need to verify the account. Can you give me the username and password again? A surprising number of people would fall for this obvious scam. There is no limit as to how elaborate this can be. The more information that is given by the caller, the more realistic or believable the call is. Again, never give your password to anyone. No legitimate customer service representative will ask for this information.
These are the basic methods that we are aware of for hacking an AOL®, Yahoo®, Hotmail® or any other dial-up or on-line password. Hopefully this will answer some questions and help you protect yourself against these attacks
Saturday, November 28, 2009
Tuesday, November 17, 2009
WinZip Pro

winzip 12 bundle WinZip Pro v14.0.8652 Incl Keymaker CORE
WinZip: Simply the most popular compression utility for Windows. WinZip offers a quickly and easily zip and unzip for files and folders. It has a flexible user interface: the intuitive WinZip Wizard for first-time users and the WinZip Classic interface for power users. Winzip mainly works with ZIP files, but you can also easily work with other formats, using external tools.
Download :
http://rapidshare.com/files/293477393/WinZip.Pro.v14.0.8652.Incl.Keymaker-CORE.rar
OR
http://uploading.com/files/48ac7ebm/WinZip.Pro.v14.0.8652.Incl.Keymaker-CORE.rar/
BabyLon

Babylon Pro is the world’s leading dictionary and language translation software. Babylon offers you the most intuitive tool for all your translation needs. With Babylon you can quickly translate emails, web pages, documents, instant messages, and more. All you have to do is click on the word or text that you want to translate and a small window instantly appears with the desired results from Babylon’s extensive database of language dictionaries, glossaries and conversion tools
Features:
* Single Click activation
* Text translation – in 17 languages
* Results from the world’s leading publishers
* Encyclopedias including Wikipedia content
* Translations in more than 75 languages
* Unit Conversions – Convert currencies, measurements and time
* Writing Tools for English
* Spelling Alternatives
* Technical Requirement
Download :
http://hotfile.com/dl/15987113/f7822b8/Babylon.v8.0.2.r11-ZWT.rar.html
OR
http://rapidshare.com/files/298951073/Babylon.v8.0.2.r11-ZWT.rar
OR
http://freakshare.net/files/6y91y4xv/Babylon.v8.0.2.r11-ZWT.rar.html
Tune Up Utilities 2010
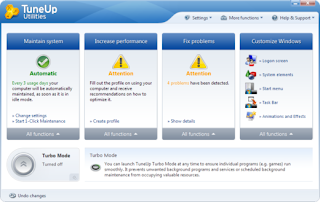
With TuneUp Utilities, your system will be faster, more comfortable and more secure. All important aspects of system configuration, security, cleanup and maintenance can be accessed through a modern graphical interface. TuneUp Utilities will optimize the performance of your PC, solve problems and help you easily customize your computer to suit your needs. TuneUp Utilities helps both beginners and experts to make Windows meet their needs in a way that is better, easier and safer. All important system options are explained in an easy way and can be turned on or off at the click of your mouse. TuneUp Utilities will then make the necessary changes in the registry or boot files automatically. We place a high value on system stability, so that Windows won’t stop working reliably. And most changes that you make can be undone in TuneUp Rescue Center – easily and safely.
Download :
http://hotfile.com/dl/16300449/10b3b2f/TuneUP.Utilities.2010.Incl.Serial.WinAll-iND.rar.html
OR
http://rapidshare.com/files/300607174/TuneUP.Utilities.2010.Incl.Serial.WinAll-iND.rar
Wednesday, September 9, 2009
QuickTime 7.6.4 Professional Edition

QuickTime 7.6.4 Professional Edition | 31.0 MB
The QuickTime family of digital media creation, delivery and playback software lets you deliver live or pre-recorded video and audio to an audience of any size. When combined with QuickTime Player and QuickTime Pro, these applications work together to provide the industry’s first end-to-end, standards-based digital media delivery system. QuickTime 7 is Apple's cutting-edge digital media software for both Mac and Windows-based computers delivers unparalleled quality for creating, playing and streaming audio and video content over the Internet. Besides playing MPEG-4 and MP3 content, it supports timecode tracks as well as MIDI standards such as the Roland Sound Canvas and GS format extensions. It also supports key standards for web streaming, including HTTP, RTP and RTSP. Plus, it supports every major file format for images, including JPEG, BMP, PICT, PNG and GIF. QuickTime 7 features an ultra efficient new H.264 video codec delivering stunning quality at remarkably low data rates from 3G to iChat AV to HD.
New features in QuickTime 7 Pro for Windows:
• Create H.264 video. Create incredible-looking video for any use, from 3G for mobile devices to HD.
• Create surround audio. Create a rich multimedia experience by adding multichannel audio to your movie.
• Floating controls. Easily access functions like pause, play, fast-forward, and rewind while watching full-screen movies.
• Background exporting. Export your movie in the background and continue with your next playback or editing task.
• Improved movie authoring. The all-new Movie Properties facilitates simple and efficient movie authoring.
• Automate with VB Script. Automate your QuickTime workflow with native VB Script support in QuickTime 7. Developers can also use VB Script to access the new QuickTime Active X control for creating custom multimedia applications.
Homepage - http://www.apple.com/quicktime/
Download:
Labels:
app 2009,
download,
free,
full,
NICE WINDOWS APPLICATION
Thursday, September 3, 2009
u tube downloader
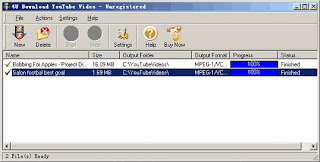
Are you looking for a software to download youtube video? 4U Download YouTube Video is the profect solution for you. 4U Download YouTube Video is a powerful video software to download videos from YouTube and save as many different video formats, such as MPEG, AVI, DivX, XviD, MP4, 3GP, WMV, ASF, MOV, QT, VOB, etc. It also allows you to save your favorite online videos to audio formats which includes MP3, AC3, AAC, M4A. With 4U Download YouTube Video, you can download and transfer YouTube video into your PC, iPod, PSP, iPhone, PDA, PocketPC, Cell Phone, or other portable video device, including Archos, iRiver, or Creative Zen Vision. Now, 4U Download YouTube Video not only supports YouTube video, but also downloads videos from Google video and Myspace.
Download :
http://hotfile.com/dl/11374004/a65e0a2/4U.Download.YouTube.Video.v2.6.9-SUN.rar.html
OR
http://rapidshare.com/files/274974689/4U.Download.YouTube.Video.v2.6.9-SUN.rar
Easy DVD Creator
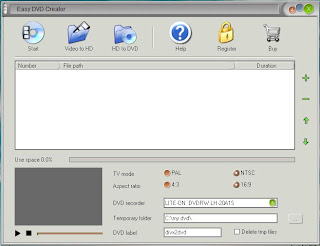
Easy DVD Creator provides you a handy tool to convert AVI/DIVX/XVID/DIV, MPEG/MPG/DAT, WMV/ASF/ASX, RM/RMVB, MOV/QT, 3GP/3G2, MP4/M4V, FLV and TOD into DVDs that you can watch in your home DVD player.With Easy DVD Creator, you can easily turn the vacation, wedding and family movies into DVDs that you can burn and share with your friends and family! Easily create DVDs in your own home! Just add video files into the file list, click “Start” and it’s done.
Download :
http://hotfile.com/dl/11374007/9633f22/Easy.DVD.Creator.v2.0.16.WinALL.Incl.Keygen-BLiZZARD.rar.html
OR
http://rapidshare.com/files/274974697/Easy.DVD.Creator.v2.0.16.WinALL.Incl.Keygen-BLiZZARD.rar
Tuesday, September 1, 2009
Ultra ISO PREMIUM

rcwdqxn9ble2dv37r4i8 EZB Systems UltraISO Premium Edition v9 3 5 2716 Multilingual Retail Incl Keymaker ZWT
UltraISO Premium Edition, is an ISO CD/DVD image file creating/editing/converting tool and a bootable CD/DVD maker , it can directly edit the CD/DVD image file and extract files and folders from it, as well as directly make ISO files from your CD/DVD-ROM or hard disk. At the same time, you can maintain the ISO bootable information, thus creating your own bootable CD/DVDs. You now have the power to make and edit your own ISO files, and then burn them to CD/DVD for your own needs.
Note : Type The Password , Don't copy & paste .
Password : irfree.com
Download :
http://hotfile.com/dl/11200211/6cd9f18/EZB.Systems.UltraISO.Premium.Edition.v9.3.5.2716.Multilingual.Retail.Incl.Keymaker-ZWT.rar.html
OR
http://rapidshare.com/files/273845620/EZB.Systems.UltraISO.Premium.Edition.v9.3.5.2716.Multilingual.Retail.Incl.Keymaker-ZWT.rar
Friday, August 28, 2009
BOOKS

# Publisher: Weatherhill (September 2, 2003)
# Language: English
# ISBN-10: 0834805405
# ISBN-13: 978-0834805408
Product Description
This unique work outlines the essential principles and techniques that define armed and unarmed self-defense involving common weapons. More than 1,400 outstanding photographs introduce over 350 practical techniques spanning seven basic classes of weapons--knife, short-stick, staff, cane, rope, common objects, and defense against handguns--the mastery of which provides practitioners with a range of skills that will allow them to wield almost anything as a weapon. Each weapons chapter provides an authoritative overview of important technical principles, tactics, weapon types, grips, stances, and fundamental strikes and blocks, followed by numerous self-defense applications. Introductory chapters cover weapons philosophy, energetic concepts, 106 pressure points, and a visual comparison of different martial arts, making this an invaluable resource for all martial styles. Expertly written and designed by the author of the 1,136-page Hapkido--widely acclaimed the most comprehensive book ever written on a single martial art--this exceptional work is designed to stand alone, or function as a companion text with the author's other works on martial techniques and anatomy. Regardless of the style you practice, these books will enrich your training, improve your technique, and deepen your understanding of the unique qualities embodied in your own martial art.
About the Author
Marc Tedeschi is an internationally respected artist, designer, educator, and martial arts master, who has practiced martial arts for more than 30 years, training extensively in Hapkido, Taekwondo, Jujutsu, Judo, and Karate. Mr. Tedeschi's unique ability to blend his skills as a designer, writer, and martial artist has resulted in numerous books, widely acknowledged for their design excellence, outstanding imagery, and clarity of content. He is the author of twelve works, including a unique series of general martial arts books that provide an in-depth look at the core concepts and techniques shared by a broad range of martial arts. To learn more, Google search: Marc Tedeschi or marctedeschi.

# Publisher: Bench Pr Intl (June 1, 1998)
# Language: English
# ISBN-10: 096704300X
# ISBN-13: 978-0967043005
Product Description
This manual uses over 600 pages, 3,500 images, and 100,000 words to display many hundreds of mixed martial arts techniques, from striking, to takedowns, to ground control, to submission.
About the Author
Author Kirik Jenness has nearly 30 years experience in the martial arts, runs The World's Best Source for Mixed Martial Arts Information, and is the Commissioner of the North American Grappling Association.
Thursday, August 13, 2009
NICE APPLICATIONS
Perfect Uninstaller is a better and easier way for you to completely uninstall any unwanted application that standard Windows Add/Remove Program can’t remove.
Have you ever been bothered with software applications that can’t be uninstalled by the standard Windows Add/Remove Programs? You are in the right place!
Note : Type The Password , Don't copy & paste .
Password : irfree.com
Download (links are interchangeable) :
http://rapidshare.com/files/265912969/Perfect.Uninstaller.v6.3.3.6.WinALL.Cracked-CzW.rar
OR
http://www.megaupload.com/?d=2I2W5MP5
SWF Decompile Expert is the fastest and most reliable solution for users especially to completely decompile any SWF file. With the high-speed decompiling encoder, you really won’t find any application that decompiles faster than SWF Decompile Expert!
Note : Type The Password , Don't copy & paste .
Password : irfree.com
Download (links are interchangeable) :
http://rapidshare.com/files/265912143/SWF.Decompile.Expert.v3.0.2.99.WinALL.Regged-CzW.rar
OR
http://www.megaupload.com/?d=GUFJ8TKE
Final Uninstaller provides an easy and comprehensive solution for uninstalling unwanted programs, whether it’s running properly on your computer now or it has been corrupted and leaves some remnants after a failed uninstall or install. It also cleans up all junk files and removes invalid registry entries to optimize your PC efficiency. This easy-to-use Final Uninstaller allows you to say goodbye to a host of uninstall problems and give your computer maximum performance.
Note : Type The Password , Don't copy & paste .
Password : irfree.com
Download (links are interchangeable) :
http://rapidshare.com/files/265909399/Final.Uninstaller.v2.5.2.WinALL.Incl.Keygen-CzW.rar
OR
http://www.megaupload.com/?d=NC1AD9G3
Lyrics are displayed automatically and if they are not found, you can add them yourself. Also the looks can be customised by configuring options such as – font colour, font type, background colour etc.
Note : Type The Password , Don't copy & paste .
Password : irfree.com
Download (links are interchangeable) :
http://rapidshare.com/files/265800408/MiniLyrics.v6.6.319.Incl.Keygen-JANOSiK.rar
OR
http://www.megaupload.com/?d=Q8HQ9HZG
Protector Plus detects all types of viruses, trojans and worms before they enter the computer and removes the virus.Protector Plus ensures that the computer is virus free. Protector Plus is packed with many useful features like email scanning, InstaUpdate, scheduled scanning, memory scanning,de-activation of viruses in memory, quarantine, user defined scan tasks, rescue disk, compressed files scanning and many more.Protector Plus is a tool that will surely help you protect your PC from numerous types of malware threats.The email scan feature scans all the emails received before they enter the Inbox and ensures that all the emails and attachments are virus free. On detecting an infected email the virus will be removed.
Note : Type The Password , Don't copy & paste .
Password : irfree.com
Download (links are interchangeable) :
http://rapidshare.com/files/265790278/Protector.Plus.2009.v8.0.E03.Incl.Keymaker-CORE.rar
OR
http://www.megaupload.com/?d=L77DK9X3
Wednesday, July 22, 2009
Knowlege-free & share
Here i will share some of the knowledge of different sites that i have learnt from my personal experience during my 1st & 2nd year in college.
List of sites to download free ebooks:
1. http://congloi.info/ {free & nice; one of my Fav.;just create a free account and download numerous number of useful ebooks}
2. http://www.downloadfreepdf.com
3. http://www.knowfree.net
List of site to download free games,and different softwares:
1. http://download.cnet.com/windows/ {one of the trusted site but there are less softwares in full version but if u get one then u are really lucy coz its standard is very high}
2. http://www.filehippo.com/ {i love this site, its simply nice.i am sure u'l also like this site}
3. http://www.brothersoft.com/
List of sites for hollywood movie download:
1. http://www.divxcrawler.com/ {i like this site but limited movies are available but its direct download}
2. http://www.irfree.com/ {i like this site because of its collections of games,movies and many more thing.so wnjoy!!!}
List of site do download bollywood movies:
1. http://www.filmijoy.com/ {nice site to download latest bolly movies}
List of sites to download free songs:
1.http://songs.pk/ {i simply download my collection of bollywood songs from this site,it simply has nice collections}
Subscribe to:
Comments (Atom)



